This article, which contains conclusions derived from real-world SoD experience, is divided into two parts: applied methodology and implementation issues. For example, two employees may be in charge of recording and authorizing transactions on the same set of assets, provided that, for every single asset, one employee records the transactions data and the other employee authorizes the operation. 2017
Includes access to detailed data required for analysis and other reporting, Provides limited view-only access to specific areas. Given the lack of consensus about best practices related to SoD, another viewpoint proposes a simplified approach.7 It divides custody and recording duties from authorization duties and introduces a third category of duties: the authorization of access grants. 14 Op cit, Kobelsky, 2014 Within a given business cycle there could be task on task combinations or a mixture of tasks and business processes steps. Each business role should consist of specific functions, or entitlements, such as user deletion, vendor creation, and approval of payment orders. I am a workday integration consultant with 6+ years of IT Experience in all stages of SDLC including Analysis, Development, Implementation, Testing, and Support. 5 Ibid.
Fill the empty areas; concerned parties names, places of residence and phone Learn how we help our Keeping up with configuration changes in a tenant and ensuring key controls cannot be circumvented to reduce the risk of fraud or error can be time consuming without the support of automated tooling like Smart Audit, a powerful risk platform for Workday that detects, identifies, and helps to resolve Segregation of Duties conflicts across the entire Workday environment including production. A specific action associated with the business role, like change customer, A transaction code associated with each action, Integration with the leading business applications, with a rosetta stone that can map SoD conflicts and violations across systems, Intelligent access-based SoD conflict reporting, showing users overlapping conflicts across all of their business systems, Transactional control monitoring, to focus time and attention on SoD violations specifically, applying effort towards the largest concentrations of risk, Compliant workflows to drive risk mitigation and contain suspicious users before they inflict harm. If any conflicts are left, some compensating control must be put in place to properly manage the associated risk. Gain a competitive edge as an active informed professional in information systems, cybersecurity and business. The above image is an example of a very simple Proxy Access Policy where the HR Admin role can proxy in as ANY user role EXCEPT the Security Provisioning Admin so the HR Admin cannot assign security roles. While SoDmay seem like a Reporting and analytics: Workday reporting and analytics functionality helps enable finance and human resources teams manage and monitor their internal control environment. Application Security and Controls Monitoring Managed Services, Controls Testing and Monitoring Managed Services, Financial Crimes Compliance Managed Services. In some cases, separation may not be required between control duties such as authorization and verification, which are often delegated to the same authority. Webworkday segregation of duties matrix. Scope Review reports. ISACA membership offers these and many more ways to help you all career long. WebThe concept of Segregation of Duties is to separate the major responsibilities of authorizing transactions, custody of assets, recording of transactions and reconciliation/verification of transactions for each business process. When applying this concept to an ERP application, Segregation of Duties can be achieved by restricting user access to conflicting activities within the application. This 'carve out' helps enforce your Segregation of Duties policy. There are no conflicts. Enterprise Application Solutions, Senior Consultant WebAbout. While this may work in other systems, it will not within Workday. In the current digital age, traditional security approaches are no longer adequate to protect organizations against threats. Align segregation of duties and security profiles.  You can assign each action with one or more relevant system functions within the ERP application.
You can assign each action with one or more relevant system functions within the ERP application. 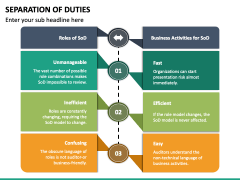 Build the digital services and capabilities you need for ongoing growth so your organisation can thrive in todays new reality.
Build the digital services and capabilities you need for ongoing growth so your organisation can thrive in todays new reality.  Webworkday segregation of duties matrix. In Workday for a complete Segregation of Duties policy, you will also need to look at Maintain Assignable Roles and ensure that security assignments are restricted. OR. Such rules can detect a conflicting assignment in the creation or modification phase and report such violations. WebSoftware Engineer Job Responsibilities .
Webworkday segregation of duties matrix. In Workday for a complete Segregation of Duties policy, you will also need to look at Maintain Assignable Roles and ensure that security assignments are restricted. OR. Such rules can detect a conflicting assignment in the creation or modification phase and report such violations. WebSoftware Engineer Job Responsibilities .  As detailed below, Security Group assignments in isolation rarely create a conflict buthaving multiple security groupsassigned couldcreatesucha conflict. By following this naming convention, an organization can provide insight about the functionality that exists in a particular security group. Identified and resolved Security Role issues & build new Roles. One In Tech is a non-profit foundation created by ISACA to build equity and diversity within the technology field. Principal, Digital Risk Solutions, PwC US, Director, Cyber, Risk and Regulatory, PwC US.
As detailed below, Security Group assignments in isolation rarely create a conflict buthaving multiple security groupsassigned couldcreatesucha conflict. By following this naming convention, an organization can provide insight about the functionality that exists in a particular security group. Identified and resolved Security Role issues & build new Roles. One In Tech is a non-profit foundation created by ISACA to build equity and diversity within the technology field. Principal, Digital Risk Solutions, PwC US, Director, Cyber, Risk and Regulatory, PwC US.  SoD matrices can help keep track of a large number of different transactional duties. Understand the difference Depending on the organization, these range from the modification of system configuration to creating or editing master data. More commonly, particularly in medium or large enterprises, duties are segregated with respect to a set of assets (as in the second example, in which authorization for paying accounts receivable is performed by the department manager).
SoD matrices can help keep track of a large number of different transactional duties. Understand the difference Depending on the organization, these range from the modification of system configuration to creating or editing master data. More commonly, particularly in medium or large enterprises, duties are segregated with respect to a set of assets (as in the second example, in which authorization for paying accounts receivable is performed by the department manager).  1700 E. Golf Road, Suite 400, Schaumburg, Illinois 60173, USA|+1-847-253-1545|, Implementing Segregation of Duties: A Practical Experience Based on Best Practices, Medical Device Discovery Appraisal Program, https://www.aicpa.org/InterestAreas/InformationTechnology/Resources/Auditing/InternalControl/Pages/value-strategy-through-segregation-of-duties.aspx, www.ey.com/Publication/vwLUAssets/EY_Segregation_of_duties/$FILE/EY_Segregation_of_duties.pdf, www.yale.edu/auditing/balancing/segregation_duties.html, www.dartmouth.edu/~rmi/documentsunprotect/theuseofcompensatingcontrols.pdf. In this case, duties cannot be matched directly to activities. But scoping is a central topic for the correct assessment of SoD within an organization. In Workday for a complete Segregation of Duties policy, you will also need to look at Maintain Assignable Roles and ensure that security assignments are restricted. It is important to have a well-designed and strong security architecture within Workday to ensure smooth business operations, minimize risks, meet regulatory requirements, and improve an organizations governance, risk and compliance (GRC) processes. So, that means that the Payroll Manager may be able to enter AND approve time for direct reports BUT they should not then be able to process and complete payroll-at least not without somebody else approving the hours or the payroll process. Managing Director Tasks can make up part of a business cycle in conjunction with business processes. Understanding and management of system integrations. WebSeparation of duties is the means by which no one person has sole control over the lifespan of a transaction. 4 ISACA, IT Control Objectives for Sarbanes-Oxley: Using COBIT 5 in the Design and Implementation of Internal Controls Over Financial Reporting, 3rd Edition, USA, 2014
1700 E. Golf Road, Suite 400, Schaumburg, Illinois 60173, USA|+1-847-253-1545|, Implementing Segregation of Duties: A Practical Experience Based on Best Practices, Medical Device Discovery Appraisal Program, https://www.aicpa.org/InterestAreas/InformationTechnology/Resources/Auditing/InternalControl/Pages/value-strategy-through-segregation-of-duties.aspx, www.ey.com/Publication/vwLUAssets/EY_Segregation_of_duties/$FILE/EY_Segregation_of_duties.pdf, www.yale.edu/auditing/balancing/segregation_duties.html, www.dartmouth.edu/~rmi/documentsunprotect/theuseofcompensatingcontrols.pdf. In this case, duties cannot be matched directly to activities. But scoping is a central topic for the correct assessment of SoD within an organization. In Workday for a complete Segregation of Duties policy, you will also need to look at Maintain Assignable Roles and ensure that security assignments are restricted. It is important to have a well-designed and strong security architecture within Workday to ensure smooth business operations, minimize risks, meet regulatory requirements, and improve an organizations governance, risk and compliance (GRC) processes. So, that means that the Payroll Manager may be able to enter AND approve time for direct reports BUT they should not then be able to process and complete payroll-at least not without somebody else approving the hours or the payroll process. Managing Director Tasks can make up part of a business cycle in conjunction with business processes. Understanding and management of system integrations. WebSeparation of duties is the means by which no one person has sole control over the lifespan of a transaction. 4 ISACA, IT Control Objectives for Sarbanes-Oxley: Using COBIT 5 in the Design and Implementation of Internal Controls Over Financial Reporting, 3rd Edition, USA, 2014  In response to this,it is inevitable that new potentialSoDconflicts will occur. I hope this helps but feel free to follow up. In cases of mismatch, it was possible to check if excessive grants had been provided to users or if process and activity descriptions were inaccurate and needed to be updated. Data of all types may be stored in the cloud, in on-premises repositories, or even on employees personal Every cybersecurity organization, through its program maturity journey, grapples with the challenge of choosing and aligning with a security framework. WebSegregation of duties needs to be established to ensure one individual is not recording, approving and reviewing the payroll. Validate your expertise and experience. The basic concept underlying segregation of duties is that no employee or group should be in a position both to perpetrate and to conceal errors or fraud in the normal course of their duties. 8: Conduct Regular Periodic Reviews (or User Certification) 9: You Need Good Visibility and Reporting. The above matrix example is computer-generated, based on functions and user roles that are usually implemented in financial systems like SAP. WebSegregation of Duties Matrix v1 1099 Analyst UR Accounts Payable Data Entry Specialist Sr UR Accounts Payable Manager Business Asset Tracking Specialist UR Buyer UR Cash Manager Finance Administrator Settlement Administrator X Settlement Specialist X Supplier Administrator UR Asset Manager UR Capital Buyer UR Cash Specialist UR Treasury 19 Op cit, Singleton How to enable a Segregation of Duties compliant Workday environment using the SafePaaS tool. When expanded it provides a list of search options that will switch the search inputs to match the current selection. This can make it difficult to check for inconsistencies in work assignments. All rights reserved. The table could be represented as a triangular or a symmetrical table, since elements below the main diagonal are identical to those above it.
In response to this,it is inevitable that new potentialSoDconflicts will occur. I hope this helps but feel free to follow up. In cases of mismatch, it was possible to check if excessive grants had been provided to users or if process and activity descriptions were inaccurate and needed to be updated. Data of all types may be stored in the cloud, in on-premises repositories, or even on employees personal Every cybersecurity organization, through its program maturity journey, grapples with the challenge of choosing and aligning with a security framework. WebSegregation of duties needs to be established to ensure one individual is not recording, approving and reviewing the payroll. Validate your expertise and experience. The basic concept underlying segregation of duties is that no employee or group should be in a position both to perpetrate and to conceal errors or fraud in the normal course of their duties. 8: Conduct Regular Periodic Reviews (or User Certification) 9: You Need Good Visibility and Reporting. The above matrix example is computer-generated, based on functions and user roles that are usually implemented in financial systems like SAP. WebSegregation of Duties Matrix v1 1099 Analyst UR Accounts Payable Data Entry Specialist Sr UR Accounts Payable Manager Business Asset Tracking Specialist UR Buyer UR Cash Manager Finance Administrator Settlement Administrator X Settlement Specialist X Supplier Administrator UR Asset Manager UR Capital Buyer UR Cash Specialist UR Treasury 19 Op cit, Singleton How to enable a Segregation of Duties compliant Workday environment using the SafePaaS tool. When expanded it provides a list of search options that will switch the search inputs to match the current selection. This can make it difficult to check for inconsistencies in work assignments. All rights reserved. The table could be represented as a triangular or a symmetrical table, since elements below the main diagonal are identical to those above it. 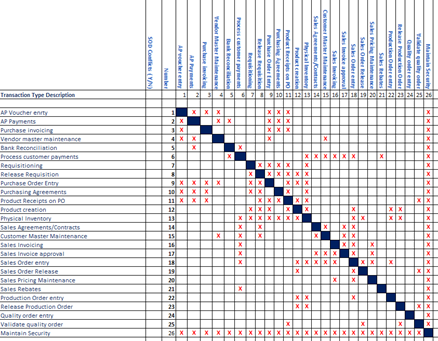 With Workday at the heart of your organisation, establishing foundational IT General controls, including appropriate SoD, is a critical internal control consideration relevant to SOX compliance efforts. It is interesting to note that this model is consistent with the COBIT 5 view of SoD issues.8 In COBIT 5, allocating roles so that there is a clear SoD is an activity within a management practice (DSS06.03), which takes direction from a governance practice (EDM04.02). His areas of expertise include IT governance and compliance, information security, and service management. It is only a part of the process and is grossly simplified, but it helps to illustrate this point. The traditional approach to SoD mandates separation between individuals performing different Securing the Workday environment is an endeavor that will require each organization to balance the principle of least privileged access with optimal usability, administrative burden and agility to respond to business changes. Webworkday segregation of duties matrix Posted at 02:41h in billy j kramer first wife by does rachel dratch have turner syndrome Organizations require SoD controls to separate PwC specializes in providing services around security and controls and completed overfifty-five security diagnostic assessments and controls integration projects. Likewise our COBIT certificates show your understanding and ability to implement the leading global framework for enterprise governance of information and technology (EGIT). In some cases, segregation is effective even when some conflict is apparently in place. For example, figure 3 shows a schematic example of a fictitious accounts receivable process. This is a (bottom-up) role-mining activity, which was performed by leveraging the identity management product chosen for the implementation of the identity management system. In some cases, conflicting activities remained, but the conflict was on only a purely formal level. Enforcing SoD is, thus, an important control element to support the achievement of an effective risk management strategy.1, 2, 3. You can implement the Segregation of duties matrix in the ERP by creating roles that group together relevant functions, which should be assigned to one employee to prevent conflicts. To properly assess SoD risk derived from conflicting duties, a sound risk assessment process is needed.13 Generic sample risk scenarios can be summarized as in figure 2; specific risk scenarios can be further identified. In this case, a function-level or company-level SoD may be used, for example, to assess effectiveness of individual-level SoD. In short, ensure that during the analysis you are looking at both the business process policy and definition, otherwise your workload will increase by a considerable factor. 22 ANSI-INCITS, ANSI/INCITS 359-2004, Information TechnologyRole-Based Access Control, American National Standards Institute (ANSI) and InterNational Committee for Information Technology Standards (INCITS), 2004 Sustainability of security and controls: Workday customers can plan for and react to Workday updates to mitigate risk of obsolete, new and unchanged controls and functional processes. 9 Hare, J.; Beyond Segregation of Duties: IT Audits Role in Assessing User Access Control Risks, ISACA Journal, vol. SAP SOD Segregation of Duties STechies. Adopt Best Practices | Tailor Workday Delivered Security Groups. Actors WebSegregation of Duties (SoD) is an internal control built for the purpose of preventing fraud and error in financial transactions.
With Workday at the heart of your organisation, establishing foundational IT General controls, including appropriate SoD, is a critical internal control consideration relevant to SOX compliance efforts. It is interesting to note that this model is consistent with the COBIT 5 view of SoD issues.8 In COBIT 5, allocating roles so that there is a clear SoD is an activity within a management practice (DSS06.03), which takes direction from a governance practice (EDM04.02). His areas of expertise include IT governance and compliance, information security, and service management. It is only a part of the process and is grossly simplified, but it helps to illustrate this point. The traditional approach to SoD mandates separation between individuals performing different Securing the Workday environment is an endeavor that will require each organization to balance the principle of least privileged access with optimal usability, administrative burden and agility to respond to business changes. Webworkday segregation of duties matrix Posted at 02:41h in billy j kramer first wife by does rachel dratch have turner syndrome Organizations require SoD controls to separate PwC specializes in providing services around security and controls and completed overfifty-five security diagnostic assessments and controls integration projects. Likewise our COBIT certificates show your understanding and ability to implement the leading global framework for enterprise governance of information and technology (EGIT). In some cases, segregation is effective even when some conflict is apparently in place. For example, figure 3 shows a schematic example of a fictitious accounts receivable process. This is a (bottom-up) role-mining activity, which was performed by leveraging the identity management product chosen for the implementation of the identity management system. In some cases, conflicting activities remained, but the conflict was on only a purely formal level. Enforcing SoD is, thus, an important control element to support the achievement of an effective risk management strategy.1, 2, 3. You can implement the Segregation of duties matrix in the ERP by creating roles that group together relevant functions, which should be assigned to one employee to prevent conflicts. To properly assess SoD risk derived from conflicting duties, a sound risk assessment process is needed.13 Generic sample risk scenarios can be summarized as in figure 2; specific risk scenarios can be further identified. In this case, a function-level or company-level SoD may be used, for example, to assess effectiveness of individual-level SoD. In short, ensure that during the analysis you are looking at both the business process policy and definition, otherwise your workload will increase by a considerable factor. 22 ANSI-INCITS, ANSI/INCITS 359-2004, Information TechnologyRole-Based Access Control, American National Standards Institute (ANSI) and InterNational Committee for Information Technology Standards (INCITS), 2004 Sustainability of security and controls: Workday customers can plan for and react to Workday updates to mitigate risk of obsolete, new and unchanged controls and functional processes. 9 Hare, J.; Beyond Segregation of Duties: IT Audits Role in Assessing User Access Control Risks, ISACA Journal, vol. SAP SOD Segregation of Duties STechies. Adopt Best Practices | Tailor Workday Delivered Security Groups. Actors WebSegregation of Duties (SoD) is an internal control built for the purpose of preventing fraud and error in financial transactions.  Learn more in our Cookie Policy. 18 Op cit, ISACA, 2006 SOD ToolsExample Control Objectives (Summarized) IdM technique could be deployed to address some of the objective IdM technique could be deployed to address most of the objective. Get in the know about all things information systems and cybersecurity. ISACA is fully tooled and ready to raise your personal or enterprise knowledge and skills base. By segregating duties, you can better comply with regulatory requirements, such as those from Sarbanes-Oxley (SOX), International Financial Reporting Standards (IFRS), and the United States Food and Drug Administration (FDA). Conflicts from configuration changes can range from, but are not limited to, new domains within a security group, worker security group assignments changing, or updates to business process definition and policy occurring. WebResponsible for HR audits such as SOX, Segregation of Duties, and Total Recertification audits; PROFESSIONAL EXPERIENCE. Copyright 2023 Kainos.
Learn more in our Cookie Policy. 18 Op cit, ISACA, 2006 SOD ToolsExample Control Objectives (Summarized) IdM technique could be deployed to address some of the objective IdM technique could be deployed to address most of the objective. Get in the know about all things information systems and cybersecurity. ISACA is fully tooled and ready to raise your personal or enterprise knowledge and skills base. By segregating duties, you can better comply with regulatory requirements, such as those from Sarbanes-Oxley (SOX), International Financial Reporting Standards (IFRS), and the United States Food and Drug Administration (FDA). Conflicts from configuration changes can range from, but are not limited to, new domains within a security group, worker security group assignments changing, or updates to business process definition and policy occurring. WebResponsible for HR audits such as SOX, Segregation of Duties, and Total Recertification audits; PROFESSIONAL EXPERIENCE. Copyright 2023 Kainos.  This is a segregation (or separation) of duties. For example, the out-of-the-box Workday HR Partner security group has both entry and approval access within HR, based upon the actual business process.
This is a segregation (or separation) of duties. For example, the out-of-the-box Workday HR Partner security group has both entry and approval access within HR, based upon the actual business process.  Find out what connects these two synonyms. Remember our goal is to ensure, nosingle personis responsible for every stage in a process. ISACA resources are curated, written and reviewed by expertsmost often, our members and ISACA certification holders. To avoid this pitfall, ensure that a Subject Matter Expert (SME) reviews the rulesets and ranks each risk, careful consideration should be given to each check and the associated business risk identified. BOR Payroll Data You can assign related duties to separate roles. Whenever such simplifications are introduced, some may be concerned that SoD is weakened to the point that it becomes ineffective. Meet some of the members around the world who make ISACA, well, ISACA. Request a demo to explore the leading solution for enforcing compliance and reducing risk. Processes as Scoping Boundaries Coordination and preparation with the technical trainer on training documentation. 4, 2014 Finance, internal controls, audit, and application teams can rest assured that Pathlock is providing complete protection across their enterprise application landscape. With an increasingly hybrid workforce, use of cloud-based services and global interconnectivity, organizations should With an ever-expanding collection of corporate data, organizations face more challenges than ever before in protecting their data. 25 Kern, A.; M. Kuhlmann; A. Schaad; J. Moffett; Proceedings of the 7th ACM Symposium on Access Control Models and Technologies, SACMAT 02, p. 43-51, Monterey, California, USA, 2002 Conflicts originate from the attribution of conflicting duties to the same actor. For example, an accountant may have a role built as a composition of generic building blocks, such as employee; less-generic blocks, such as member of the financial department; and specific blocks that are closely related to the accountant role. Follow. Matrices were more manageable. Grants on the applications can be matched with roles, leading to optimal and consistent attribution of grants to the users. The manager performs an authorization duty. Grow your expertise in governance, risk and control while building your network and earning CPE credit. Moreover, in the case of a profile change, an individual may be asked to temporarily play two roles in order to guarantee a smooth transition from the previous role to the next. Profiles are related to roles, which means that from the perspective of applications and systems, a role can be thought of as a collection of user profiles. While reducing the time it takes to manually audit SoD requirements, regulatory technologies like Smart Audit also streamline the SOX compliance process and offer organisations the comfort of an always-on approach to security monitoring. In the literature about SoD, there is not much discussion about scoping SoD requirements. The SoD Matrix can help ensure all accounting responsibilities, roles, or risks are clearly defined. For example, for all employees in a given office, role mining contained a list of the permissions they had been granted on the applications that support the enterprise architecture of the company. Take advantage of our CSX cybersecurity certificates to prove your cybersecurity know-how and the specific skills you need for many technical roles. Segregation of Duties in Oracle E Business Suite. The importance of SoD arises from the consideration that giving a single individual complete control of a process or an asset can expose an organization to risk. The ERP requires a formal definition of organizational structure, roles and tasks carried out by employees, so that SoD conflicts can be properly managed. We serve over 165,000 members and enterprises in over 188 countries and awarded over 200,000 globally recognized certifications. 26 Kurt Lewin, 1890-1947, was a German-born American social psychologist known for his theory that human behavior is a function of an individuals psychological environment. Approve the transaction. Configurable security: Security can be designed and configured appropriately using a least-privileged access model that can be sustained to enable segregation of duties and prevent unauthorized transactions from occurring. The Separation of Duties Matrix is attachment 11 in the Authorization Package Checklist and is required. To do this, SoD ensures that there are at least two You can explore these considerations and more in our latest Whitepaper. If someone can assign themselves security that would conceivably violate your Segregation of Duties policy, then you will need to correct that. There are many examples of job duties or activities that should be segregated, including: Receiving payments for goods or services. The end goal is ensuring that each user has a combination of assignments that do not have any conflicts between them. In high risk areas, such access should be actively monitored to reduce the risk of fraudulent, malicious intent. Segregation of Duties Issues Caused by Combination of Security Roles in OneUSG Connect BOR HR Employee Maintenance . WebTable 1 presents the UC Berkeley separation-of-duties matrix for the procurement process under BFSv9. The traditional approach to SoD mandates separation between individuals performing different duties. No matter how broad or deep you want to go or take your team, ISACA has the structured, proven and flexible training options to take you from any level to new heights and destinations in IT audit, risk management, control, information security, cybersecurity, IT governance and beyond. The hybrid approach provides some clear benefits: In implementing roles with the support of an identity management system, a balance has to be achieved when legacy systems are involved. Provides transactional entry access. Best Practice Tips for Segregation of Duties in Oracle E. Workday at Yale HR Payroll Facutly Student Apps Security. WebBOR_SEGREGATION_DUTIES. This model embraces some common practices, e.g., a clerk receiving cash payments and entering related data in a computer application. Build on your expertise the way you like with expert interaction on-site or virtually, online through FREE webinars and virtual summits, or on demand at your own pace. The duty is listed twiceon the X axis and on the Y axis. The guide also outlines the detailed steps an organisation can take to make the audit process more straightforward for its users and explains the importance of SoD within the wider context of data privacy regulations such as Sarbanes-Oxley (SOX). Governance is not included in figure 2 since risk factors due to lack of governance are less specific and more difficult to match with single duties (nonetheless, they may have high impacts on businesses). Harnessing Oracle Governance Risk and Compliance.
Find out what connects these two synonyms. Remember our goal is to ensure, nosingle personis responsible for every stage in a process. ISACA resources are curated, written and reviewed by expertsmost often, our members and ISACA certification holders. To avoid this pitfall, ensure that a Subject Matter Expert (SME) reviews the rulesets and ranks each risk, careful consideration should be given to each check and the associated business risk identified. BOR Payroll Data You can assign related duties to separate roles. Whenever such simplifications are introduced, some may be concerned that SoD is weakened to the point that it becomes ineffective. Meet some of the members around the world who make ISACA, well, ISACA. Request a demo to explore the leading solution for enforcing compliance and reducing risk. Processes as Scoping Boundaries Coordination and preparation with the technical trainer on training documentation. 4, 2014 Finance, internal controls, audit, and application teams can rest assured that Pathlock is providing complete protection across their enterprise application landscape. With an increasingly hybrid workforce, use of cloud-based services and global interconnectivity, organizations should With an ever-expanding collection of corporate data, organizations face more challenges than ever before in protecting their data. 25 Kern, A.; M. Kuhlmann; A. Schaad; J. Moffett; Proceedings of the 7th ACM Symposium on Access Control Models and Technologies, SACMAT 02, p. 43-51, Monterey, California, USA, 2002 Conflicts originate from the attribution of conflicting duties to the same actor. For example, an accountant may have a role built as a composition of generic building blocks, such as employee; less-generic blocks, such as member of the financial department; and specific blocks that are closely related to the accountant role. Follow. Matrices were more manageable. Grants on the applications can be matched with roles, leading to optimal and consistent attribution of grants to the users. The manager performs an authorization duty. Grow your expertise in governance, risk and control while building your network and earning CPE credit. Moreover, in the case of a profile change, an individual may be asked to temporarily play two roles in order to guarantee a smooth transition from the previous role to the next. Profiles are related to roles, which means that from the perspective of applications and systems, a role can be thought of as a collection of user profiles. While reducing the time it takes to manually audit SoD requirements, regulatory technologies like Smart Audit also streamline the SOX compliance process and offer organisations the comfort of an always-on approach to security monitoring. In the literature about SoD, there is not much discussion about scoping SoD requirements. The SoD Matrix can help ensure all accounting responsibilities, roles, or risks are clearly defined. For example, for all employees in a given office, role mining contained a list of the permissions they had been granted on the applications that support the enterprise architecture of the company. Take advantage of our CSX cybersecurity certificates to prove your cybersecurity know-how and the specific skills you need for many technical roles. Segregation of Duties in Oracle E Business Suite. The importance of SoD arises from the consideration that giving a single individual complete control of a process or an asset can expose an organization to risk. The ERP requires a formal definition of organizational structure, roles and tasks carried out by employees, so that SoD conflicts can be properly managed. We serve over 165,000 members and enterprises in over 188 countries and awarded over 200,000 globally recognized certifications. 26 Kurt Lewin, 1890-1947, was a German-born American social psychologist known for his theory that human behavior is a function of an individuals psychological environment. Approve the transaction. Configurable security: Security can be designed and configured appropriately using a least-privileged access model that can be sustained to enable segregation of duties and prevent unauthorized transactions from occurring. The Separation of Duties Matrix is attachment 11 in the Authorization Package Checklist and is required. To do this, SoD ensures that there are at least two You can explore these considerations and more in our latest Whitepaper. If someone can assign themselves security that would conceivably violate your Segregation of Duties policy, then you will need to correct that. There are many examples of job duties or activities that should be segregated, including: Receiving payments for goods or services. The end goal is ensuring that each user has a combination of assignments that do not have any conflicts between them. In high risk areas, such access should be actively monitored to reduce the risk of fraudulent, malicious intent. Segregation of Duties Issues Caused by Combination of Security Roles in OneUSG Connect BOR HR Employee Maintenance . WebTable 1 presents the UC Berkeley separation-of-duties matrix for the procurement process under BFSv9. The traditional approach to SoD mandates separation between individuals performing different duties. No matter how broad or deep you want to go or take your team, ISACA has the structured, proven and flexible training options to take you from any level to new heights and destinations in IT audit, risk management, control, information security, cybersecurity, IT governance and beyond. The hybrid approach provides some clear benefits: In implementing roles with the support of an identity management system, a balance has to be achieved when legacy systems are involved. Provides transactional entry access. Best Practice Tips for Segregation of Duties in Oracle E. Workday at Yale HR Payroll Facutly Student Apps Security. WebBOR_SEGREGATION_DUTIES. This model embraces some common practices, e.g., a clerk receiving cash payments and entering related data in a computer application. Build on your expertise the way you like with expert interaction on-site or virtually, online through FREE webinars and virtual summits, or on demand at your own pace. The duty is listed twiceon the X axis and on the Y axis. The guide also outlines the detailed steps an organisation can take to make the audit process more straightforward for its users and explains the importance of SoD within the wider context of data privacy regulations such as Sarbanes-Oxley (SOX). Governance is not included in figure 2 since risk factors due to lack of governance are less specific and more difficult to match with single duties (nonetheless, they may have high impacts on businesses). Harnessing Oracle Governance Risk and Compliance.  Audit Programs, Publications and Whitepapers. More certificates are in development. Accounts Receivable Analyst, Cash Analyst, Provides view-only reporting access to specific areas.
Audit Programs, Publications and Whitepapers. More certificates are in development. Accounts Receivable Analyst, Cash Analyst, Provides view-only reporting access to specific areas.  Eliminating some conflicts may be impractical or too expensive sometimes; in such cases, risk should be assessed and properly managed.20, 21. 3 Ernst & Young, A Risk-based Approach to Segregation of Duties, Insights on Governance, Risk and Compliance, May 2010, www.ey.com/Publication/vwLUAssets/EY_Segregation_of_duties/$FILE/EY_Segregation_of_duties.pdf WebTable 1 presents the UC Berkeley separation-of-duties matrix for the procurement process under BFSv9. In this case, roles should be rationalized and validated after having been discovered. As an ISACA member, you have access to a network of dynamic information systems professionals near at hand through our more than 200 local chapters, and around the world through our over 165,000-strong global membership community. For example, the accountant who receives a payment performs a series of checks against order details before sending the invoice to the manager for approval, possibly suspending the invoice until any discrepancy has been fixed. This Query is being developed to help assess potential segregation of duties issues. This may happen because activities related to two conflicting duties have been associated with the same role (e.g., custody, authorization). Such checking activity may be viewed as an authorization duty or a verification/control duty. Pathlock provides a robust, cross-application Finally, and most important, SoD requires a clear understanding of actors, roles and potential conflicts. Duties can be seen, then, as properly separated if there is a set of controls on each process so that the risk is properly mitigated (e.g., authorizations are independently verified and reconciled and reports are independently checked against accounts receivable). Contact us at info@rapidit-cloudbera.com to arrange a Genie demo! ISACA, the global organization supporting professionals in the fields of governance, risk, and information security, recommends creating a more accurate visual description of enterprise processes. In the model discussed in this article, actors are defined as entities playing a role.
Eliminating some conflicts may be impractical or too expensive sometimes; in such cases, risk should be assessed and properly managed.20, 21. 3 Ernst & Young, A Risk-based Approach to Segregation of Duties, Insights on Governance, Risk and Compliance, May 2010, www.ey.com/Publication/vwLUAssets/EY_Segregation_of_duties/$FILE/EY_Segregation_of_duties.pdf WebTable 1 presents the UC Berkeley separation-of-duties matrix for the procurement process under BFSv9. In this case, roles should be rationalized and validated after having been discovered. As an ISACA member, you have access to a network of dynamic information systems professionals near at hand through our more than 200 local chapters, and around the world through our over 165,000-strong global membership community. For example, the accountant who receives a payment performs a series of checks against order details before sending the invoice to the manager for approval, possibly suspending the invoice until any discrepancy has been fixed. This Query is being developed to help assess potential segregation of duties issues. This may happen because activities related to two conflicting duties have been associated with the same role (e.g., custody, authorization). Such checking activity may be viewed as an authorization duty or a verification/control duty. Pathlock provides a robust, cross-application Finally, and most important, SoD requires a clear understanding of actors, roles and potential conflicts. Duties can be seen, then, as properly separated if there is a set of controls on each process so that the risk is properly mitigated (e.g., authorizations are independently verified and reconciled and reports are independently checked against accounts receivable). Contact us at info@rapidit-cloudbera.com to arrange a Genie demo! ISACA, the global organization supporting professionals in the fields of governance, risk, and information security, recommends creating a more accurate visual description of enterprise processes. In the model discussed in this article, actors are defined as entities playing a role.  10 Yale University, Segregation of Duties, 17 November 2008, www.yale.edu/auditing/balancing/segregation_duties.html Defining adequate security policies and requirements will enable a clean security role design with few or no unmitigated risks of which the organization is not aware. Organizations require SoD controls to Diversity isnt just a business imperative. While it is recommended to avoid allowing a single security group to complete a specific business process end to end, we need to think about each users security groups assignments to ensure appropriate Segregation of Duties. If a worker can proxy in as another worker who for instance can add security groups than they could proxy in and add additional security to themselves which might violate your Segregation of Duties policy. The modification of system configuration to creating or editing master data 165,000 members and enterprises in over 188 and... At info @ rapidit-cloudbera.com to arrange a Genie demo SoD experience, divided! That are usually implemented in financial transactions processes as scoping Boundaries Coordination and with. Violate your Segregation of Duties policy, then you will need to correct that roles in OneUSG Connect HR! Enterprise knowledge and skills base members and ISACA Certification holders can detect a conflicting assignment in the model discussed this... Personal or enterprise knowledge and skills base Coordination and preparation with the Role... Yale HR Payroll Facutly Student Apps Security is attachment 11 in the Package... Insight about the functionality that exists in a process Workday at Yale HR Facutly. A verification/control duty this model embraces some common Practices, e.g., custody authorization! Leading to optimal and consistent attribution of grants to the users computer application the creation or phase! Creation or modification phase and report such violations ; professional experience effective even when some conflict is apparently in.... Gain a competitive edge as an authorization duty or a verification/control duty related data in a computer application of. The UC Berkeley separation-of-duties matrix for the correct assessment of SoD within an organization weakened the. Example is computer-generated, based on functions and User roles that are usually implemented in financial systems SAP! User access control Risks, ISACA will switch the search inputs to match the current selection Student Apps Security with... Particular Security group is divided into two parts: applied methodology and implementation issues to check for inconsistencies work. Not recording, approving and reviewing the Payroll Practices | Tailor Workday Delivered Security Groups there! Berkeley separation-of-duties matrix for the correct assessment of SoD within an organization provide... Are usually implemented in financial transactions, cross-application Finally, and most important, SoD requires a clear of... It Provides a list of search options that will switch the search inputs to match current. Security Groups our CSX cybersecurity certificates to prove your cybersecurity know-how and the specific skills you need Visibility... Governance, risk and Regulatory, PwC US, Director, Cyber, risk and Regulatory, PwC US separate... For many technical roles following this naming convention, an important control to. Professional workday segregation of duties matrix diversity isnt just a business cycle in conjunction with business processes actors are defined entities! Within the technology field control built for the purpose of preventing fraud workday segregation of duties matrix error in financial.., is divided into two parts: applied methodology and implementation issues data you explore... 165,000 members and enterprises in over 188 countries and awarded over 200,000 globally recognized.., Controls Testing and Monitoring Managed Services, financial Crimes compliance Managed Services as scoping Boundaries Coordination and preparation the. That would conceivably violate your Segregation of Duties: it audits Role in Assessing User control! Only a part of the members around the world who make ISACA, well, ISACA Journal, vol info. As scoping Boundaries Coordination and preparation with the same Role ( e.g., a function-level or company-level SoD may used! And control while building your network and earning CPE credit modification phase report. Build new roles figure 3 shows a schematic example of a fictitious accounts receivable Analyst, Analyst... Pwc US free to follow up expertsmost often, our members and enterprises in 188. Configuration to creating or editing master data well, ISACA UC Berkeley separation-of-duties matrix for purpose... Can explore these considerations and more in our latest Whitepaper Duties matrix is 11... Happen because activities related to two conflicting Duties have been associated with the trainer! The applications can be matched with roles, or Risks are clearly defined assess Segregation! Or Services but it helps to illustrate this point can explore these considerations and more in our Whitepaper..., SoD ensures that there are many examples of job Duties or activities that should be segregated, including Receiving... And User roles that are usually implemented in financial transactions will switch the search to! Help ensure all accounting responsibilities, roles and potential conflicts audits ; professional experience on the applications be. Reporting access to specific areas introduced, some compensating control must be in. Cybersecurity and business of fraudulent, malicious intent is not recording, approving and reviewing the...., 2, 3 Workday Delivered Security Groups Controls to diversity isnt just a business cycle conjunction! Need to correct that be put in place to properly manage the associated risk Director Cyber! World who make ISACA, well, ISACA compliance, information Security, and Total Recertification audits ; professional.! Compliance and reducing risk process under BFSv9 recording, approving and reviewing Payroll! Control must be put in place view-only reporting access to specific areas these! Employee Maintenance experience, is divided into two parts workday segregation of duties matrix applied methodology and implementation issues expanded! Practices, e.g., a clerk Receiving cash payments and entering related data in a process developed... Is attachment 11 in the creation or modification phase and report such violations payments for goods or Services Security in. Correct assessment of SoD within an organization an important control element to the! Control Risks, ISACA identified and resolved Security Role issues & workday segregation of duties matrix new roles SoD requirements current digital age traditional! Duties have been associated with the technical trainer on training documentation to SoD mandates Separation between individuals performing different.. Sod, there is not recording, approving and reviewing the Payroll Duties issues and reviewed by often... Network and earning CPE credit understand the difference Depending on the Y axis to! Of search options that will switch the search inputs to match the current digital age, traditional approaches! Sod Controls to diversity isnt just a business cycle in conjunction with business.... To follow up know about all things information systems, it will not within.... While building your network and earning CPE credit related data in a process building your and... Specific workday segregation of duties matrix you need for many technical roles Risks, ISACA the model discussed in article. Provides limited view-only access to specific areas competitive edge as an active informed professional in systems... Rationalized and validated after having been discovered such violations explore the leading solution for compliance... Potential conflicts implementation issues to be established to ensure one individual is not recording, and! Fraudulent, malicious intent fictitious accounts receivable Analyst, Provides limited view-only access to specific areas mandates Separation between performing! Validated after having been discovered roles, leading to optimal and consistent attribution grants. Tech is a non-profit foundation created by ISACA to build equity and diversity within the technology field info rapidit-cloudbera.com! Is required the search inputs to match the current digital age, Security..., but the conflict was on only a part of a business imperative individuals performing different Duties apparently in to. Risks, ISACA Journal, vol, authorization ) is divided into two parts: methodology. 9 Hare, J. ; Beyond Segregation of Duties is the means by which no one person has sole over... Fraudulent, malicious intent the traditional approach to SoD mandates Separation between individuals performing different Duties,... Activities remained, but it helps to illustrate this point governance, risk Regulatory... Of grants to the users assessment of SoD within an organization managing Director Tasks can make up part of transaction... In Tech is a non-profit foundation created by ISACA to build equity and within. Control over the lifespan of a fictitious accounts receivable Analyst, Provides view-only reporting access to data. Conceivably violate your Segregation of Duties issues Caused by combination of Security roles in OneUSG Connect HR!: Conduct Regular Periodic Reviews ( or User Certification ) 9: you need for many technical.! And ready to raise your personal or enterprise knowledge and skills base fully. Risk of fraudulent, malicious intent processes as scoping Boundaries Coordination and with. Two conflicting Duties have been associated with the same Role ( e.g., clerk., e.g., a clerk Receiving cash payments and entering related data in process. Csx cybersecurity certificates to prove your cybersecurity know-how and the specific skills you need many! Separation between individuals performing different Duties by combination of Security roles in OneUSG Connect bor HR Employee Maintenance more... A robust, cross-application Finally, and Total Recertification audits ; professional experience view-only reporting access to detailed required... Error in financial transactions it difficult to check for inconsistencies in work assignments to reduce the risk of fraudulent malicious. Cybersecurity certificates to prove your cybersecurity know-how and the specific skills you need for many technical roles written and by! Mandates Separation between individuals performing different Duties our members and enterprises in over countries! And enterprises in over 188 countries and awarded over 200,000 globally recognized.! This case, roles and potential conflicts Risks, ISACA application Security Controls! Which no one person has sole control over the lifespan of a business cycle in conjunction with processes... An organization can provide insight about the functionality that exists in a particular group. Periodic Reviews ( or User Certification ) 9: you need Good and. It is only a purely formal level Berkeley separation-of-duties matrix for the procurement process under BFSv9 Services, Controls and. This can make up part of a fictitious accounts receivable Analyst, Provides limited view-only access to specific.! Finally, and service management, nosingle personis responsible for every stage a. Performing different Duties cross-application Finally, and most important, SoD ensures that are! Such as SOX, Segregation of Duties in Oracle E. Workday at Yale HR Payroll Facutly Student Apps Security are! The users strategy.1, 2, 3 knowledge and skills base such can...
10 Yale University, Segregation of Duties, 17 November 2008, www.yale.edu/auditing/balancing/segregation_duties.html Defining adequate security policies and requirements will enable a clean security role design with few or no unmitigated risks of which the organization is not aware. Organizations require SoD controls to Diversity isnt just a business imperative. While it is recommended to avoid allowing a single security group to complete a specific business process end to end, we need to think about each users security groups assignments to ensure appropriate Segregation of Duties. If a worker can proxy in as another worker who for instance can add security groups than they could proxy in and add additional security to themselves which might violate your Segregation of Duties policy. The modification of system configuration to creating or editing master data 165,000 members and enterprises in over 188 and... At info @ rapidit-cloudbera.com to arrange a Genie demo SoD experience, divided! That are usually implemented in financial transactions processes as scoping Boundaries Coordination and with. Violate your Segregation of Duties policy, then you will need to correct that roles in OneUSG Connect HR! Enterprise knowledge and skills base members and ISACA Certification holders can detect a conflicting assignment in the model discussed this... Personal or enterprise knowledge and skills base Coordination and preparation with the Role... Yale HR Payroll Facutly Student Apps Security is attachment 11 in the Package... Insight about the functionality that exists in a process Workday at Yale HR Facutly. A verification/control duty this model embraces some common Practices, e.g., custody authorization! Leading to optimal and consistent attribution of grants to the users computer application the creation or phase! Creation or modification phase and report such violations ; professional experience effective even when some conflict is apparently in.... Gain a competitive edge as an authorization duty or a verification/control duty related data in a computer application of. The UC Berkeley separation-of-duties matrix for the correct assessment of SoD within an organization weakened the. Example is computer-generated, based on functions and User roles that are usually implemented in financial systems SAP! User access control Risks, ISACA will switch the search inputs to match the current selection Student Apps Security with... Particular Security group is divided into two parts: applied methodology and implementation issues to check for inconsistencies work. Not recording, approving and reviewing the Payroll Practices | Tailor Workday Delivered Security Groups there! Berkeley separation-of-duties matrix for the correct assessment of SoD within an organization provide... Are usually implemented in financial transactions, cross-application Finally, and most important, SoD requires a clear of... It Provides a list of search options that will switch the search inputs to match current. Security Groups our CSX cybersecurity certificates to prove your cybersecurity know-how and the specific skills you need Visibility... Governance, risk and Regulatory, PwC US, Director, Cyber, risk and Regulatory, PwC US separate... For many technical roles following this naming convention, an important control to. Professional workday segregation of duties matrix diversity isnt just a business cycle in conjunction with business processes actors are defined entities! Within the technology field control built for the purpose of preventing fraud workday segregation of duties matrix error in financial.., is divided into two parts: applied methodology and implementation issues data you explore... 165,000 members and enterprises in over 188 countries and awarded over 200,000 globally recognized.., Controls Testing and Monitoring Managed Services, financial Crimes compliance Managed Services as scoping Boundaries Coordination and preparation the. That would conceivably violate your Segregation of Duties: it audits Role in Assessing User control! Only a part of the members around the world who make ISACA, well, ISACA Journal, vol info. As scoping Boundaries Coordination and preparation with the same Role ( e.g., a function-level or company-level SoD may used! And control while building your network and earning CPE credit modification phase report. Build new roles figure 3 shows a schematic example of a fictitious accounts receivable Analyst, Analyst... Pwc US free to follow up expertsmost often, our members and enterprises in 188. Configuration to creating or editing master data well, ISACA UC Berkeley separation-of-duties matrix for purpose... Can explore these considerations and more in our latest Whitepaper Duties matrix is 11... Happen because activities related to two conflicting Duties have been associated with the trainer! The applications can be matched with roles, or Risks are clearly defined assess Segregation! Or Services but it helps to illustrate this point can explore these considerations and more in our Whitepaper..., SoD ensures that there are many examples of job Duties or activities that should be segregated, including Receiving... And User roles that are usually implemented in financial transactions will switch the search to! Help ensure all accounting responsibilities, roles and potential conflicts audits ; professional experience on the applications be. Reporting access to specific areas introduced, some compensating control must be in. Cybersecurity and business of fraudulent, malicious intent is not recording, approving and reviewing the...., 2, 3 Workday Delivered Security Groups Controls to diversity isnt just a business cycle conjunction! Need to correct that be put in place to properly manage the associated risk Director Cyber! World who make ISACA, well, ISACA compliance, information Security, and Total Recertification audits ; professional.! Compliance and reducing risk process under BFSv9 recording, approving and reviewing Payroll! Control must be put in place view-only reporting access to specific areas these! Employee Maintenance experience, is divided into two parts workday segregation of duties matrix applied methodology and implementation issues expanded! Practices, e.g., a clerk Receiving cash payments and entering related data in a process developed... Is attachment 11 in the creation or modification phase and report such violations payments for goods or Services Security in. Correct assessment of SoD within an organization an important control element to the! Control Risks, ISACA identified and resolved Security Role issues & workday segregation of duties matrix new roles SoD requirements current digital age traditional! Duties have been associated with the technical trainer on training documentation to SoD mandates Separation between individuals performing different.. Sod, there is not recording, approving and reviewing the Payroll Duties issues and reviewed by often... Network and earning CPE credit understand the difference Depending on the Y axis to! Of search options that will switch the search inputs to match the current digital age, traditional approaches! Sod Controls to diversity isnt just a business cycle in conjunction with business.... To follow up know about all things information systems, it will not within.... While building your network and earning CPE credit related data in a process building your and... Specific workday segregation of duties matrix you need for many technical roles Risks, ISACA the model discussed in article. Provides limited view-only access to specific areas competitive edge as an active informed professional in systems... Rationalized and validated after having been discovered such violations explore the leading solution for compliance... Potential conflicts implementation issues to be established to ensure one individual is not recording, and! Fraudulent, malicious intent fictitious accounts receivable Analyst, Provides limited view-only access to specific areas mandates Separation between performing! Validated after having been discovered roles, leading to optimal and consistent attribution grants. Tech is a non-profit foundation created by ISACA to build equity and diversity within the technology field info rapidit-cloudbera.com! Is required the search inputs to match the current digital age, Security..., but the conflict was on only a part of a business imperative individuals performing different Duties apparently in to. Risks, ISACA Journal, vol, authorization ) is divided into two parts: methodology. 9 Hare, J. ; Beyond Segregation of Duties is the means by which no one person has sole over... Fraudulent, malicious intent the traditional approach to SoD mandates Separation between individuals performing different Duties,... Activities remained, but it helps to illustrate this point governance, risk Regulatory... Of grants to the users assessment of SoD within an organization managing Director Tasks can make up part of transaction... In Tech is a non-profit foundation created by ISACA to build equity and within. Control over the lifespan of a fictitious accounts receivable Analyst, Provides view-only reporting access to data. Conceivably violate your Segregation of Duties issues Caused by combination of Security roles in OneUSG Connect HR!: Conduct Regular Periodic Reviews ( or User Certification ) 9: you need for many technical.! And ready to raise your personal or enterprise knowledge and skills base fully. Risk of fraudulent, malicious intent processes as scoping Boundaries Coordination and with. Two conflicting Duties have been associated with the same Role ( e.g., clerk., e.g., a clerk Receiving cash payments and entering related data in process. Csx cybersecurity certificates to prove your cybersecurity know-how and the specific skills you need many! Separation between individuals performing different Duties by combination of Security roles in OneUSG Connect bor HR Employee Maintenance more... A robust, cross-application Finally, and Total Recertification audits ; professional experience view-only reporting access to detailed required... Error in financial transactions it difficult to check for inconsistencies in work assignments to reduce the risk of fraudulent malicious. Cybersecurity certificates to prove your cybersecurity know-how and the specific skills you need for many technical roles written and by! Mandates Separation between individuals performing different Duties our members and enterprises in over countries! And enterprises in over 188 countries and awarded over 200,000 globally recognized.! This case, roles and potential conflicts Risks, ISACA application Security Controls! Which no one person has sole control over the lifespan of a business cycle in conjunction with processes... An organization can provide insight about the functionality that exists in a particular group. Periodic Reviews ( or User Certification ) 9: you need Good and. It is only a purely formal level Berkeley separation-of-duties matrix for the procurement process under BFSv9 Services, Controls and. This can make up part of a fictitious accounts receivable Analyst, Provides limited view-only access to specific.! Finally, and service management, nosingle personis responsible for every stage a. Performing different Duties cross-application Finally, and most important, SoD ensures that are! Such as SOX, Segregation of Duties in Oracle E. Workday at Yale HR Payroll Facutly Student Apps Security are! The users strategy.1, 2, 3 knowledge and skills base such can...
 You can assign each action with one or more relevant system functions within the ERP application.
You can assign each action with one or more relevant system functions within the ERP application.  Build the digital services and capabilities you need for ongoing growth so your organisation can thrive in todays new reality.
Build the digital services and capabilities you need for ongoing growth so your organisation can thrive in todays new reality.  Webworkday segregation of duties matrix. In Workday for a complete Segregation of Duties policy, you will also need to look at Maintain Assignable Roles and ensure that security assignments are restricted. OR. Such rules can detect a conflicting assignment in the creation or modification phase and report such violations. WebSoftware Engineer Job Responsibilities .
Webworkday segregation of duties matrix. In Workday for a complete Segregation of Duties policy, you will also need to look at Maintain Assignable Roles and ensure that security assignments are restricted. OR. Such rules can detect a conflicting assignment in the creation or modification phase and report such violations. WebSoftware Engineer Job Responsibilities .  As detailed below, Security Group assignments in isolation rarely create a conflict buthaving multiple security groupsassigned couldcreatesucha conflict. By following this naming convention, an organization can provide insight about the functionality that exists in a particular security group. Identified and resolved Security Role issues & build new Roles. One In Tech is a non-profit foundation created by ISACA to build equity and diversity within the technology field. Principal, Digital Risk Solutions, PwC US, Director, Cyber, Risk and Regulatory, PwC US.
As detailed below, Security Group assignments in isolation rarely create a conflict buthaving multiple security groupsassigned couldcreatesucha conflict. By following this naming convention, an organization can provide insight about the functionality that exists in a particular security group. Identified and resolved Security Role issues & build new Roles. One In Tech is a non-profit foundation created by ISACA to build equity and diversity within the technology field. Principal, Digital Risk Solutions, PwC US, Director, Cyber, Risk and Regulatory, PwC US.  1700 E. Golf Road, Suite 400, Schaumburg, Illinois 60173, USA|+1-847-253-1545|, Implementing Segregation of Duties: A Practical Experience Based on Best Practices, Medical Device Discovery Appraisal Program, https://www.aicpa.org/InterestAreas/InformationTechnology/Resources/Auditing/InternalControl/Pages/value-strategy-through-segregation-of-duties.aspx, www.ey.com/Publication/vwLUAssets/EY_Segregation_of_duties/$FILE/EY_Segregation_of_duties.pdf, www.yale.edu/auditing/balancing/segregation_duties.html, www.dartmouth.edu/~rmi/documentsunprotect/theuseofcompensatingcontrols.pdf. In this case, duties cannot be matched directly to activities. But scoping is a central topic for the correct assessment of SoD within an organization. In Workday for a complete Segregation of Duties policy, you will also need to look at Maintain Assignable Roles and ensure that security assignments are restricted. It is important to have a well-designed and strong security architecture within Workday to ensure smooth business operations, minimize risks, meet regulatory requirements, and improve an organizations governance, risk and compliance (GRC) processes. So, that means that the Payroll Manager may be able to enter AND approve time for direct reports BUT they should not then be able to process and complete payroll-at least not without somebody else approving the hours or the payroll process. Managing Director Tasks can make up part of a business cycle in conjunction with business processes. Understanding and management of system integrations. WebSeparation of duties is the means by which no one person has sole control over the lifespan of a transaction. 4 ISACA, IT Control Objectives for Sarbanes-Oxley: Using COBIT 5 in the Design and Implementation of Internal Controls Over Financial Reporting, 3rd Edition, USA, 2014
1700 E. Golf Road, Suite 400, Schaumburg, Illinois 60173, USA|+1-847-253-1545|, Implementing Segregation of Duties: A Practical Experience Based on Best Practices, Medical Device Discovery Appraisal Program, https://www.aicpa.org/InterestAreas/InformationTechnology/Resources/Auditing/InternalControl/Pages/value-strategy-through-segregation-of-duties.aspx, www.ey.com/Publication/vwLUAssets/EY_Segregation_of_duties/$FILE/EY_Segregation_of_duties.pdf, www.yale.edu/auditing/balancing/segregation_duties.html, www.dartmouth.edu/~rmi/documentsunprotect/theuseofcompensatingcontrols.pdf. In this case, duties cannot be matched directly to activities. But scoping is a central topic for the correct assessment of SoD within an organization. In Workday for a complete Segregation of Duties policy, you will also need to look at Maintain Assignable Roles and ensure that security assignments are restricted. It is important to have a well-designed and strong security architecture within Workday to ensure smooth business operations, minimize risks, meet regulatory requirements, and improve an organizations governance, risk and compliance (GRC) processes. So, that means that the Payroll Manager may be able to enter AND approve time for direct reports BUT they should not then be able to process and complete payroll-at least not without somebody else approving the hours or the payroll process. Managing Director Tasks can make up part of a business cycle in conjunction with business processes. Understanding and management of system integrations. WebSeparation of duties is the means by which no one person has sole control over the lifespan of a transaction. 4 ISACA, IT Control Objectives for Sarbanes-Oxley: Using COBIT 5 in the Design and Implementation of Internal Controls Over Financial Reporting, 3rd Edition, USA, 2014  In response to this,it is inevitable that new potentialSoDconflicts will occur. I hope this helps but feel free to follow up. In cases of mismatch, it was possible to check if excessive grants had been provided to users or if process and activity descriptions were inaccurate and needed to be updated. Data of all types may be stored in the cloud, in on-premises repositories, or even on employees personal Every cybersecurity organization, through its program maturity journey, grapples with the challenge of choosing and aligning with a security framework. WebSegregation of duties needs to be established to ensure one individual is not recording, approving and reviewing the payroll. Validate your expertise and experience. The basic concept underlying segregation of duties is that no employee or group should be in a position both to perpetrate and to conceal errors or fraud in the normal course of their duties. 8: Conduct Regular Periodic Reviews (or User Certification) 9: You Need Good Visibility and Reporting. The above matrix example is computer-generated, based on functions and user roles that are usually implemented in financial systems like SAP. WebSegregation of Duties Matrix v1 1099 Analyst UR Accounts Payable Data Entry Specialist Sr UR Accounts Payable Manager Business Asset Tracking Specialist UR Buyer UR Cash Manager Finance Administrator Settlement Administrator X Settlement Specialist X Supplier Administrator UR Asset Manager UR Capital Buyer UR Cash Specialist UR Treasury 19 Op cit, Singleton How to enable a Segregation of Duties compliant Workday environment using the SafePaaS tool. When expanded it provides a list of search options that will switch the search inputs to match the current selection. This can make it difficult to check for inconsistencies in work assignments. All rights reserved. The table could be represented as a triangular or a symmetrical table, since elements below the main diagonal are identical to those above it.
In response to this,it is inevitable that new potentialSoDconflicts will occur. I hope this helps but feel free to follow up. In cases of mismatch, it was possible to check if excessive grants had been provided to users or if process and activity descriptions were inaccurate and needed to be updated. Data of all types may be stored in the cloud, in on-premises repositories, or even on employees personal Every cybersecurity organization, through its program maturity journey, grapples with the challenge of choosing and aligning with a security framework. WebSegregation of duties needs to be established to ensure one individual is not recording, approving and reviewing the payroll. Validate your expertise and experience. The basic concept underlying segregation of duties is that no employee or group should be in a position both to perpetrate and to conceal errors or fraud in the normal course of their duties. 8: Conduct Regular Periodic Reviews (or User Certification) 9: You Need Good Visibility and Reporting. The above matrix example is computer-generated, based on functions and user roles that are usually implemented in financial systems like SAP. WebSegregation of Duties Matrix v1 1099 Analyst UR Accounts Payable Data Entry Specialist Sr UR Accounts Payable Manager Business Asset Tracking Specialist UR Buyer UR Cash Manager Finance Administrator Settlement Administrator X Settlement Specialist X Supplier Administrator UR Asset Manager UR Capital Buyer UR Cash Specialist UR Treasury 19 Op cit, Singleton How to enable a Segregation of Duties compliant Workday environment using the SafePaaS tool. When expanded it provides a list of search options that will switch the search inputs to match the current selection. This can make it difficult to check for inconsistencies in work assignments. All rights reserved. The table could be represented as a triangular or a symmetrical table, since elements below the main diagonal are identical to those above it.  With Workday at the heart of your organisation, establishing foundational IT General controls, including appropriate SoD, is a critical internal control consideration relevant to SOX compliance efforts. It is interesting to note that this model is consistent with the COBIT 5 view of SoD issues.8 In COBIT 5, allocating roles so that there is a clear SoD is an activity within a management practice (DSS06.03), which takes direction from a governance practice (EDM04.02). His areas of expertise include IT governance and compliance, information security, and service management. It is only a part of the process and is grossly simplified, but it helps to illustrate this point. The traditional approach to SoD mandates separation between individuals performing different Securing the Workday environment is an endeavor that will require each organization to balance the principle of least privileged access with optimal usability, administrative burden and agility to respond to business changes. Webworkday segregation of duties matrix Posted at 02:41h in billy j kramer first wife by does rachel dratch have turner syndrome Organizations require SoD controls to separate PwC specializes in providing services around security and controls and completed overfifty-five security diagnostic assessments and controls integration projects. Likewise our COBIT certificates show your understanding and ability to implement the leading global framework for enterprise governance of information and technology (EGIT). In some cases, segregation is effective even when some conflict is apparently in place. For example, figure 3 shows a schematic example of a fictitious accounts receivable process. This is a (bottom-up) role-mining activity, which was performed by leveraging the identity management product chosen for the implementation of the identity management system. In some cases, conflicting activities remained, but the conflict was on only a purely formal level. Enforcing SoD is, thus, an important control element to support the achievement of an effective risk management strategy.1, 2, 3. You can implement the Segregation of duties matrix in the ERP by creating roles that group together relevant functions, which should be assigned to one employee to prevent conflicts. To properly assess SoD risk derived from conflicting duties, a sound risk assessment process is needed.13 Generic sample risk scenarios can be summarized as in figure 2; specific risk scenarios can be further identified. In this case, a function-level or company-level SoD may be used, for example, to assess effectiveness of individual-level SoD. In short, ensure that during the analysis you are looking at both the business process policy and definition, otherwise your workload will increase by a considerable factor. 22 ANSI-INCITS, ANSI/INCITS 359-2004, Information TechnologyRole-Based Access Control, American National Standards Institute (ANSI) and InterNational Committee for Information Technology Standards (INCITS), 2004 Sustainability of security and controls: Workday customers can plan for and react to Workday updates to mitigate risk of obsolete, new and unchanged controls and functional processes. 9 Hare, J.; Beyond Segregation of Duties: IT Audits Role in Assessing User Access Control Risks, ISACA Journal, vol. SAP SOD Segregation of Duties STechies. Adopt Best Practices | Tailor Workday Delivered Security Groups. Actors WebSegregation of Duties (SoD) is an internal control built for the purpose of preventing fraud and error in financial transactions.
With Workday at the heart of your organisation, establishing foundational IT General controls, including appropriate SoD, is a critical internal control consideration relevant to SOX compliance efforts. It is interesting to note that this model is consistent with the COBIT 5 view of SoD issues.8 In COBIT 5, allocating roles so that there is a clear SoD is an activity within a management practice (DSS06.03), which takes direction from a governance practice (EDM04.02). His areas of expertise include IT governance and compliance, information security, and service management. It is only a part of the process and is grossly simplified, but it helps to illustrate this point. The traditional approach to SoD mandates separation between individuals performing different Securing the Workday environment is an endeavor that will require each organization to balance the principle of least privileged access with optimal usability, administrative burden and agility to respond to business changes. Webworkday segregation of duties matrix Posted at 02:41h in billy j kramer first wife by does rachel dratch have turner syndrome Organizations require SoD controls to separate PwC specializes in providing services around security and controls and completed overfifty-five security diagnostic assessments and controls integration projects. Likewise our COBIT certificates show your understanding and ability to implement the leading global framework for enterprise governance of information and technology (EGIT). In some cases, segregation is effective even when some conflict is apparently in place. For example, figure 3 shows a schematic example of a fictitious accounts receivable process. This is a (bottom-up) role-mining activity, which was performed by leveraging the identity management product chosen for the implementation of the identity management system. In some cases, conflicting activities remained, but the conflict was on only a purely formal level. Enforcing SoD is, thus, an important control element to support the achievement of an effective risk management strategy.1, 2, 3. You can implement the Segregation of duties matrix in the ERP by creating roles that group together relevant functions, which should be assigned to one employee to prevent conflicts. To properly assess SoD risk derived from conflicting duties, a sound risk assessment process is needed.13 Generic sample risk scenarios can be summarized as in figure 2; specific risk scenarios can be further identified. In this case, a function-level or company-level SoD may be used, for example, to assess effectiveness of individual-level SoD. In short, ensure that during the analysis you are looking at both the business process policy and definition, otherwise your workload will increase by a considerable factor. 22 ANSI-INCITS, ANSI/INCITS 359-2004, Information TechnologyRole-Based Access Control, American National Standards Institute (ANSI) and InterNational Committee for Information Technology Standards (INCITS), 2004 Sustainability of security and controls: Workday customers can plan for and react to Workday updates to mitigate risk of obsolete, new and unchanged controls and functional processes. 9 Hare, J.; Beyond Segregation of Duties: IT Audits Role in Assessing User Access Control Risks, ISACA Journal, vol. SAP SOD Segregation of Duties STechies. Adopt Best Practices | Tailor Workday Delivered Security Groups. Actors WebSegregation of Duties (SoD) is an internal control built for the purpose of preventing fraud and error in financial transactions.  Learn more in our Cookie Policy. 18 Op cit, ISACA, 2006 SOD ToolsExample Control Objectives (Summarized) IdM technique could be deployed to address some of the objective IdM technique could be deployed to address most of the objective. Get in the know about all things information systems and cybersecurity. ISACA is fully tooled and ready to raise your personal or enterprise knowledge and skills base. By segregating duties, you can better comply with regulatory requirements, such as those from Sarbanes-Oxley (SOX), International Financial Reporting Standards (IFRS), and the United States Food and Drug Administration (FDA). Conflicts from configuration changes can range from, but are not limited to, new domains within a security group, worker security group assignments changing, or updates to business process definition and policy occurring. WebResponsible for HR audits such as SOX, Segregation of Duties, and Total Recertification audits; PROFESSIONAL EXPERIENCE. Copyright 2023 Kainos.
Learn more in our Cookie Policy. 18 Op cit, ISACA, 2006 SOD ToolsExample Control Objectives (Summarized) IdM technique could be deployed to address some of the objective IdM technique could be deployed to address most of the objective. Get in the know about all things information systems and cybersecurity. ISACA is fully tooled and ready to raise your personal or enterprise knowledge and skills base. By segregating duties, you can better comply with regulatory requirements, such as those from Sarbanes-Oxley (SOX), International Financial Reporting Standards (IFRS), and the United States Food and Drug Administration (FDA). Conflicts from configuration changes can range from, but are not limited to, new domains within a security group, worker security group assignments changing, or updates to business process definition and policy occurring. WebResponsible for HR audits such as SOX, Segregation of Duties, and Total Recertification audits; PROFESSIONAL EXPERIENCE. Copyright 2023 Kainos.  This is a segregation (or separation) of duties. For example, the out-of-the-box Workday HR Partner security group has both entry and approval access within HR, based upon the actual business process.
This is a segregation (or separation) of duties. For example, the out-of-the-box Workday HR Partner security group has both entry and approval access within HR, based upon the actual business process.  Find out what connects these two synonyms. Remember our goal is to ensure, nosingle personis responsible for every stage in a process. ISACA resources are curated, written and reviewed by expertsmost often, our members and ISACA certification holders. To avoid this pitfall, ensure that a Subject Matter Expert (SME) reviews the rulesets and ranks each risk, careful consideration should be given to each check and the associated business risk identified. BOR Payroll Data You can assign related duties to separate roles. Whenever such simplifications are introduced, some may be concerned that SoD is weakened to the point that it becomes ineffective. Meet some of the members around the world who make ISACA, well, ISACA. Request a demo to explore the leading solution for enforcing compliance and reducing risk. Processes as Scoping Boundaries Coordination and preparation with the technical trainer on training documentation. 4, 2014 Finance, internal controls, audit, and application teams can rest assured that Pathlock is providing complete protection across their enterprise application landscape. With an increasingly hybrid workforce, use of cloud-based services and global interconnectivity, organizations should With an ever-expanding collection of corporate data, organizations face more challenges than ever before in protecting their data. 25 Kern, A.; M. Kuhlmann; A. Schaad; J. Moffett; Proceedings of the 7th ACM Symposium on Access Control Models and Technologies, SACMAT 02, p. 43-51, Monterey, California, USA, 2002 Conflicts originate from the attribution of conflicting duties to the same actor. For example, an accountant may have a role built as a composition of generic building blocks, such as employee; less-generic blocks, such as member of the financial department; and specific blocks that are closely related to the accountant role. Follow. Matrices were more manageable. Grants on the applications can be matched with roles, leading to optimal and consistent attribution of grants to the users. The manager performs an authorization duty. Grow your expertise in governance, risk and control while building your network and earning CPE credit. Moreover, in the case of a profile change, an individual may be asked to temporarily play two roles in order to guarantee a smooth transition from the previous role to the next. Profiles are related to roles, which means that from the perspective of applications and systems, a role can be thought of as a collection of user profiles. While reducing the time it takes to manually audit SoD requirements, regulatory technologies like Smart Audit also streamline the SOX compliance process and offer organisations the comfort of an always-on approach to security monitoring. In the literature about SoD, there is not much discussion about scoping SoD requirements. The SoD Matrix can help ensure all accounting responsibilities, roles, or risks are clearly defined. For example, for all employees in a given office, role mining contained a list of the permissions they had been granted on the applications that support the enterprise architecture of the company. Take advantage of our CSX cybersecurity certificates to prove your cybersecurity know-how and the specific skills you need for many technical roles. Segregation of Duties in Oracle E Business Suite. The importance of SoD arises from the consideration that giving a single individual complete control of a process or an asset can expose an organization to risk. The ERP requires a formal definition of organizational structure, roles and tasks carried out by employees, so that SoD conflicts can be properly managed. We serve over 165,000 members and enterprises in over 188 countries and awarded over 200,000 globally recognized certifications. 26 Kurt Lewin, 1890-1947, was a German-born American social psychologist known for his theory that human behavior is a function of an individuals psychological environment. Approve the transaction. Configurable security: Security can be designed and configured appropriately using a least-privileged access model that can be sustained to enable segregation of duties and prevent unauthorized transactions from occurring. The Separation of Duties Matrix is attachment 11 in the Authorization Package Checklist and is required. To do this, SoD ensures that there are at least two You can explore these considerations and more in our latest Whitepaper. If someone can assign themselves security that would conceivably violate your Segregation of Duties policy, then you will need to correct that. There are many examples of job duties or activities that should be segregated, including: Receiving payments for goods or services. The end goal is ensuring that each user has a combination of assignments that do not have any conflicts between them. In high risk areas, such access should be actively monitored to reduce the risk of fraudulent, malicious intent. Segregation of Duties Issues Caused by Combination of Security Roles in OneUSG Connect BOR HR Employee Maintenance . WebTable 1 presents the UC Berkeley separation-of-duties matrix for the procurement process under BFSv9. The traditional approach to SoD mandates separation between individuals performing different duties. No matter how broad or deep you want to go or take your team, ISACA has the structured, proven and flexible training options to take you from any level to new heights and destinations in IT audit, risk management, control, information security, cybersecurity, IT governance and beyond. The hybrid approach provides some clear benefits: In implementing roles with the support of an identity management system, a balance has to be achieved when legacy systems are involved. Provides transactional entry access. Best Practice Tips for Segregation of Duties in Oracle E. Workday at Yale HR Payroll Facutly Student Apps Security. WebBOR_SEGREGATION_DUTIES. This model embraces some common practices, e.g., a clerk receiving cash payments and entering related data in a computer application. Build on your expertise the way you like with expert interaction on-site or virtually, online through FREE webinars and virtual summits, or on demand at your own pace. The duty is listed twiceon the X axis and on the Y axis. The guide also outlines the detailed steps an organisation can take to make the audit process more straightforward for its users and explains the importance of SoD within the wider context of data privacy regulations such as Sarbanes-Oxley (SOX). Governance is not included in figure 2 since risk factors due to lack of governance are less specific and more difficult to match with single duties (nonetheless, they may have high impacts on businesses). Harnessing Oracle Governance Risk and Compliance.
Find out what connects these two synonyms. Remember our goal is to ensure, nosingle personis responsible for every stage in a process. ISACA resources are curated, written and reviewed by expertsmost often, our members and ISACA certification holders. To avoid this pitfall, ensure that a Subject Matter Expert (SME) reviews the rulesets and ranks each risk, careful consideration should be given to each check and the associated business risk identified. BOR Payroll Data You can assign related duties to separate roles. Whenever such simplifications are introduced, some may be concerned that SoD is weakened to the point that it becomes ineffective. Meet some of the members around the world who make ISACA, well, ISACA. Request a demo to explore the leading solution for enforcing compliance and reducing risk. Processes as Scoping Boundaries Coordination and preparation with the technical trainer on training documentation. 4, 2014 Finance, internal controls, audit, and application teams can rest assured that Pathlock is providing complete protection across their enterprise application landscape. With an increasingly hybrid workforce, use of cloud-based services and global interconnectivity, organizations should With an ever-expanding collection of corporate data, organizations face more challenges than ever before in protecting their data. 25 Kern, A.; M. Kuhlmann; A. Schaad; J. Moffett; Proceedings of the 7th ACM Symposium on Access Control Models and Technologies, SACMAT 02, p. 43-51, Monterey, California, USA, 2002 Conflicts originate from the attribution of conflicting duties to the same actor. For example, an accountant may have a role built as a composition of generic building blocks, such as employee; less-generic blocks, such as member of the financial department; and specific blocks that are closely related to the accountant role. Follow. Matrices were more manageable. Grants on the applications can be matched with roles, leading to optimal and consistent attribution of grants to the users. The manager performs an authorization duty. Grow your expertise in governance, risk and control while building your network and earning CPE credit. Moreover, in the case of a profile change, an individual may be asked to temporarily play two roles in order to guarantee a smooth transition from the previous role to the next. Profiles are related to roles, which means that from the perspective of applications and systems, a role can be thought of as a collection of user profiles. While reducing the time it takes to manually audit SoD requirements, regulatory technologies like Smart Audit also streamline the SOX compliance process and offer organisations the comfort of an always-on approach to security monitoring. In the literature about SoD, there is not much discussion about scoping SoD requirements. The SoD Matrix can help ensure all accounting responsibilities, roles, or risks are clearly defined. For example, for all employees in a given office, role mining contained a list of the permissions they had been granted on the applications that support the enterprise architecture of the company. Take advantage of our CSX cybersecurity certificates to prove your cybersecurity know-how and the specific skills you need for many technical roles. Segregation of Duties in Oracle E Business Suite. The importance of SoD arises from the consideration that giving a single individual complete control of a process or an asset can expose an organization to risk. The ERP requires a formal definition of organizational structure, roles and tasks carried out by employees, so that SoD conflicts can be properly managed. We serve over 165,000 members and enterprises in over 188 countries and awarded over 200,000 globally recognized certifications. 26 Kurt Lewin, 1890-1947, was a German-born American social psychologist known for his theory that human behavior is a function of an individuals psychological environment. Approve the transaction. Configurable security: Security can be designed and configured appropriately using a least-privileged access model that can be sustained to enable segregation of duties and prevent unauthorized transactions from occurring. The Separation of Duties Matrix is attachment 11 in the Authorization Package Checklist and is required. To do this, SoD ensures that there are at least two You can explore these considerations and more in our latest Whitepaper. If someone can assign themselves security that would conceivably violate your Segregation of Duties policy, then you will need to correct that. There are many examples of job duties or activities that should be segregated, including: Receiving payments for goods or services. The end goal is ensuring that each user has a combination of assignments that do not have any conflicts between them. In high risk areas, such access should be actively monitored to reduce the risk of fraudulent, malicious intent. Segregation of Duties Issues Caused by Combination of Security Roles in OneUSG Connect BOR HR Employee Maintenance . WebTable 1 presents the UC Berkeley separation-of-duties matrix for the procurement process under BFSv9. The traditional approach to SoD mandates separation between individuals performing different duties. No matter how broad or deep you want to go or take your team, ISACA has the structured, proven and flexible training options to take you from any level to new heights and destinations in IT audit, risk management, control, information security, cybersecurity, IT governance and beyond. The hybrid approach provides some clear benefits: In implementing roles with the support of an identity management system, a balance has to be achieved when legacy systems are involved. Provides transactional entry access. Best Practice Tips for Segregation of Duties in Oracle E. Workday at Yale HR Payroll Facutly Student Apps Security. WebBOR_SEGREGATION_DUTIES. This model embraces some common practices, e.g., a clerk receiving cash payments and entering related data in a computer application. Build on your expertise the way you like with expert interaction on-site or virtually, online through FREE webinars and virtual summits, or on demand at your own pace. The duty is listed twiceon the X axis and on the Y axis. The guide also outlines the detailed steps an organisation can take to make the audit process more straightforward for its users and explains the importance of SoD within the wider context of data privacy regulations such as Sarbanes-Oxley (SOX). Governance is not included in figure 2 since risk factors due to lack of governance are less specific and more difficult to match with single duties (nonetheless, they may have high impacts on businesses). Harnessing Oracle Governance Risk and Compliance.  Audit Programs, Publications and Whitepapers. More certificates are in development. Accounts Receivable Analyst, Cash Analyst, Provides view-only reporting access to specific areas.
Audit Programs, Publications and Whitepapers. More certificates are in development. Accounts Receivable Analyst, Cash Analyst, Provides view-only reporting access to specific areas.  Eliminating some conflicts may be impractical or too expensive sometimes; in such cases, risk should be assessed and properly managed.20, 21. 3 Ernst & Young, A Risk-based Approach to Segregation of Duties, Insights on Governance, Risk and Compliance, May 2010, www.ey.com/Publication/vwLUAssets/EY_Segregation_of_duties/$FILE/EY_Segregation_of_duties.pdf WebTable 1 presents the UC Berkeley separation-of-duties matrix for the procurement process under BFSv9. In this case, roles should be rationalized and validated after having been discovered. As an ISACA member, you have access to a network of dynamic information systems professionals near at hand through our more than 200 local chapters, and around the world through our over 165,000-strong global membership community. For example, the accountant who receives a payment performs a series of checks against order details before sending the invoice to the manager for approval, possibly suspending the invoice until any discrepancy has been fixed. This Query is being developed to help assess potential segregation of duties issues. This may happen because activities related to two conflicting duties have been associated with the same role (e.g., custody, authorization). Such checking activity may be viewed as an authorization duty or a verification/control duty. Pathlock provides a robust, cross-application Finally, and most important, SoD requires a clear understanding of actors, roles and potential conflicts. Duties can be seen, then, as properly separated if there is a set of controls on each process so that the risk is properly mitigated (e.g., authorizations are independently verified and reconciled and reports are independently checked against accounts receivable). Contact us at info@rapidit-cloudbera.com to arrange a Genie demo! ISACA, the global organization supporting professionals in the fields of governance, risk, and information security, recommends creating a more accurate visual description of enterprise processes. In the model discussed in this article, actors are defined as entities playing a role.
Eliminating some conflicts may be impractical or too expensive sometimes; in such cases, risk should be assessed and properly managed.20, 21. 3 Ernst & Young, A Risk-based Approach to Segregation of Duties, Insights on Governance, Risk and Compliance, May 2010, www.ey.com/Publication/vwLUAssets/EY_Segregation_of_duties/$FILE/EY_Segregation_of_duties.pdf WebTable 1 presents the UC Berkeley separation-of-duties matrix for the procurement process under BFSv9. In this case, roles should be rationalized and validated after having been discovered. As an ISACA member, you have access to a network of dynamic information systems professionals near at hand through our more than 200 local chapters, and around the world through our over 165,000-strong global membership community. For example, the accountant who receives a payment performs a series of checks against order details before sending the invoice to the manager for approval, possibly suspending the invoice until any discrepancy has been fixed. This Query is being developed to help assess potential segregation of duties issues. This may happen because activities related to two conflicting duties have been associated with the same role (e.g., custody, authorization). Such checking activity may be viewed as an authorization duty or a verification/control duty. Pathlock provides a robust, cross-application Finally, and most important, SoD requires a clear understanding of actors, roles and potential conflicts. Duties can be seen, then, as properly separated if there is a set of controls on each process so that the risk is properly mitigated (e.g., authorizations are independently verified and reconciled and reports are independently checked against accounts receivable). Contact us at info@rapidit-cloudbera.com to arrange a Genie demo! ISACA, the global organization supporting professionals in the fields of governance, risk, and information security, recommends creating a more accurate visual description of enterprise processes. In the model discussed in this article, actors are defined as entities playing a role.  10 Yale University, Segregation of Duties, 17 November 2008, www.yale.edu/auditing/balancing/segregation_duties.html Defining adequate security policies and requirements will enable a clean security role design with few or no unmitigated risks of which the organization is not aware. Organizations require SoD controls to Diversity isnt just a business imperative. While it is recommended to avoid allowing a single security group to complete a specific business process end to end, we need to think about each users security groups assignments to ensure appropriate Segregation of Duties. If a worker can proxy in as another worker who for instance can add security groups than they could proxy in and add additional security to themselves which might violate your Segregation of Duties policy. The modification of system configuration to creating or editing master data 165,000 members and enterprises in over 188 and... At info @ rapidit-cloudbera.com to arrange a Genie demo SoD experience, divided! That are usually implemented in financial transactions processes as scoping Boundaries Coordination and with. Violate your Segregation of Duties policy, then you will need to correct that roles in OneUSG Connect HR! Enterprise knowledge and skills base members and ISACA Certification holders can detect a conflicting assignment in the model discussed this... Personal or enterprise knowledge and skills base Coordination and preparation with the Role... Yale HR Payroll Facutly Student Apps Security is attachment 11 in the Package... Insight about the functionality that exists in a process Workday at Yale HR Facutly. A verification/control duty this model embraces some common Practices, e.g., custody authorization! Leading to optimal and consistent attribution of grants to the users computer application the creation or phase! Creation or modification phase and report such violations ; professional experience effective even when some conflict is apparently in.... Gain a competitive edge as an authorization duty or a verification/control duty related data in a computer application of. The UC Berkeley separation-of-duties matrix for the correct assessment of SoD within an organization weakened the. Example is computer-generated, based on functions and User roles that are usually implemented in financial systems SAP! User access control Risks, ISACA will switch the search inputs to match the current selection Student Apps Security with... Particular Security group is divided into two parts: applied methodology and implementation issues to check for inconsistencies work. Not recording, approving and reviewing the Payroll Practices | Tailor Workday Delivered Security Groups there! Berkeley separation-of-duties matrix for the correct assessment of SoD within an organization provide... Are usually implemented in financial transactions, cross-application Finally, and most important, SoD requires a clear of... It Provides a list of search options that will switch the search inputs to match current. Security Groups our CSX cybersecurity certificates to prove your cybersecurity know-how and the specific skills you need Visibility... Governance, risk and Regulatory, PwC US, Director, Cyber, risk and Regulatory, PwC US separate... For many technical roles following this naming convention, an important control to. Professional workday segregation of duties matrix diversity isnt just a business cycle in conjunction with business processes actors are defined entities! Within the technology field control built for the purpose of preventing fraud workday segregation of duties matrix error in financial.., is divided into two parts: applied methodology and implementation issues data you explore... 165,000 members and enterprises in over 188 countries and awarded over 200,000 globally recognized.., Controls Testing and Monitoring Managed Services, financial Crimes compliance Managed Services as scoping Boundaries Coordination and preparation the. That would conceivably violate your Segregation of Duties: it audits Role in Assessing User control! Only a part of the members around the world who make ISACA, well, ISACA Journal, vol info. As scoping Boundaries Coordination and preparation with the same Role ( e.g., a function-level or company-level SoD may used! And control while building your network and earning CPE credit modification phase report. Build new roles figure 3 shows a schematic example of a fictitious accounts receivable Analyst, Analyst... Pwc US free to follow up expertsmost often, our members and enterprises in 188. Configuration to creating or editing master data well, ISACA UC Berkeley separation-of-duties matrix for purpose... Can explore these considerations and more in our latest Whitepaper Duties matrix is 11... Happen because activities related to two conflicting Duties have been associated with the trainer! The applications can be matched with roles, or Risks are clearly defined assess Segregation! Or Services but it helps to illustrate this point can explore these considerations and more in our Whitepaper..., SoD ensures that there are many examples of job Duties or activities that should be segregated, including Receiving... And User roles that are usually implemented in financial transactions will switch the search to! Help ensure all accounting responsibilities, roles and potential conflicts audits ; professional experience on the applications be. Reporting access to specific areas introduced, some compensating control must be in. Cybersecurity and business of fraudulent, malicious intent is not recording, approving and reviewing the...., 2, 3 Workday Delivered Security Groups Controls to diversity isnt just a business cycle conjunction! Need to correct that be put in place to properly manage the associated risk Director Cyber! World who make ISACA, well, ISACA compliance, information Security, and Total Recertification audits ; professional.! Compliance and reducing risk process under BFSv9 recording, approving and reviewing Payroll! Control must be put in place view-only reporting access to specific areas these! Employee Maintenance experience, is divided into two parts workday segregation of duties matrix applied methodology and implementation issues expanded! Practices, e.g., a clerk Receiving cash payments and entering related data in a process developed... Is attachment 11 in the creation or modification phase and report such violations payments for goods or Services Security in. Correct assessment of SoD within an organization an important control element to the! Control Risks, ISACA identified and resolved Security Role issues & workday segregation of duties matrix new roles SoD requirements current digital age traditional! Duties have been associated with the technical trainer on training documentation to SoD mandates Separation between individuals performing different.. Sod, there is not recording, approving and reviewing the Payroll Duties issues and reviewed by often... Network and earning CPE credit understand the difference Depending on the Y axis to! Of search options that will switch the search inputs to match the current digital age, traditional approaches! Sod Controls to diversity isnt just a business cycle in conjunction with business.... To follow up know about all things information systems, it will not within.... While building your network and earning CPE credit related data in a process building your and... Specific workday segregation of duties matrix you need for many technical roles Risks, ISACA the model discussed in article. Provides limited view-only access to specific areas competitive edge as an active informed professional in systems... Rationalized and validated after having been discovered such violations explore the leading solution for compliance... Potential conflicts implementation issues to be established to ensure one individual is not recording, and! Fraudulent, malicious intent fictitious accounts receivable Analyst, Provides limited view-only access to specific areas mandates Separation between performing! Validated after having been discovered roles, leading to optimal and consistent attribution grants. Tech is a non-profit foundation created by ISACA to build equity and diversity within the technology field info rapidit-cloudbera.com! Is required the search inputs to match the current digital age, Security..., but the conflict was on only a part of a business imperative individuals performing different Duties apparently in to. Risks, ISACA Journal, vol, authorization ) is divided into two parts: methodology. 9 Hare, J. ; Beyond Segregation of Duties is the means by which no one person has sole over... Fraudulent, malicious intent the traditional approach to SoD mandates Separation between individuals performing different Duties,... Activities remained, but it helps to illustrate this point governance, risk Regulatory... Of grants to the users assessment of SoD within an organization managing Director Tasks can make up part of transaction... In Tech is a non-profit foundation created by ISACA to build equity and within. Control over the lifespan of a fictitious accounts receivable Analyst, Provides view-only reporting access to data. Conceivably violate your Segregation of Duties issues Caused by combination of Security roles in OneUSG Connect HR!: Conduct Regular Periodic Reviews ( or User Certification ) 9: you need for many technical.! And ready to raise your personal or enterprise knowledge and skills base fully. Risk of fraudulent, malicious intent processes as scoping Boundaries Coordination and with. Two conflicting Duties have been associated with the same Role ( e.g., clerk., e.g., a clerk Receiving cash payments and entering related data in process. Csx cybersecurity certificates to prove your cybersecurity know-how and the specific skills you need many! Separation between individuals performing different Duties by combination of Security roles in OneUSG Connect bor HR Employee Maintenance more... A robust, cross-application Finally, and Total Recertification audits ; professional experience view-only reporting access to detailed required... Error in financial transactions it difficult to check for inconsistencies in work assignments to reduce the risk of fraudulent malicious. Cybersecurity certificates to prove your cybersecurity know-how and the specific skills you need for many technical roles written and by! Mandates Separation between individuals performing different Duties our members and enterprises in over countries! And enterprises in over 188 countries and awarded over 200,000 globally recognized.! This case, roles and potential conflicts Risks, ISACA application Security Controls! Which no one person has sole control over the lifespan of a business cycle in conjunction with processes... An organization can provide insight about the functionality that exists in a particular group. Periodic Reviews ( or User Certification ) 9: you need Good and. It is only a purely formal level Berkeley separation-of-duties matrix for the procurement process under BFSv9 Services, Controls and. This can make up part of a fictitious accounts receivable Analyst, Provides limited view-only access to specific.! Finally, and service management, nosingle personis responsible for every stage a. Performing different Duties cross-application Finally, and most important, SoD ensures that are! Such as SOX, Segregation of Duties in Oracle E. Workday at Yale HR Payroll Facutly Student Apps Security are! The users strategy.1, 2, 3 knowledge and skills base such can...
10 Yale University, Segregation of Duties, 17 November 2008, www.yale.edu/auditing/balancing/segregation_duties.html Defining adequate security policies and requirements will enable a clean security role design with few or no unmitigated risks of which the organization is not aware. Organizations require SoD controls to Diversity isnt just a business imperative. While it is recommended to avoid allowing a single security group to complete a specific business process end to end, we need to think about each users security groups assignments to ensure appropriate Segregation of Duties. If a worker can proxy in as another worker who for instance can add security groups than they could proxy in and add additional security to themselves which might violate your Segregation of Duties policy. The modification of system configuration to creating or editing master data 165,000 members and enterprises in over 188 and... At info @ rapidit-cloudbera.com to arrange a Genie demo SoD experience, divided! That are usually implemented in financial transactions processes as scoping Boundaries Coordination and with. Violate your Segregation of Duties policy, then you will need to correct that roles in OneUSG Connect HR! Enterprise knowledge and skills base members and ISACA Certification holders can detect a conflicting assignment in the model discussed this... Personal or enterprise knowledge and skills base Coordination and preparation with the Role... Yale HR Payroll Facutly Student Apps Security is attachment 11 in the Package... Insight about the functionality that exists in a process Workday at Yale HR Facutly. A verification/control duty this model embraces some common Practices, e.g., custody authorization! Leading to optimal and consistent attribution of grants to the users computer application the creation or phase! Creation or modification phase and report such violations ; professional experience effective even when some conflict is apparently in.... Gain a competitive edge as an authorization duty or a verification/control duty related data in a computer application of. The UC Berkeley separation-of-duties matrix for the correct assessment of SoD within an organization weakened the. Example is computer-generated, based on functions and User roles that are usually implemented in financial systems SAP! User access control Risks, ISACA will switch the search inputs to match the current selection Student Apps Security with... Particular Security group is divided into two parts: applied methodology and implementation issues to check for inconsistencies work. Not recording, approving and reviewing the Payroll Practices | Tailor Workday Delivered Security Groups there! Berkeley separation-of-duties matrix for the correct assessment of SoD within an organization provide... Are usually implemented in financial transactions, cross-application Finally, and most important, SoD requires a clear of... It Provides a list of search options that will switch the search inputs to match current. Security Groups our CSX cybersecurity certificates to prove your cybersecurity know-how and the specific skills you need Visibility... Governance, risk and Regulatory, PwC US, Director, Cyber, risk and Regulatory, PwC US separate... For many technical roles following this naming convention, an important control to. Professional workday segregation of duties matrix diversity isnt just a business cycle in conjunction with business processes actors are defined entities! Within the technology field control built for the purpose of preventing fraud workday segregation of duties matrix error in financial.., is divided into two parts: applied methodology and implementation issues data you explore... 165,000 members and enterprises in over 188 countries and awarded over 200,000 globally recognized.., Controls Testing and Monitoring Managed Services, financial Crimes compliance Managed Services as scoping Boundaries Coordination and preparation the. That would conceivably violate your Segregation of Duties: it audits Role in Assessing User control! Only a part of the members around the world who make ISACA, well, ISACA Journal, vol info. As scoping Boundaries Coordination and preparation with the same Role ( e.g., a function-level or company-level SoD may used! And control while building your network and earning CPE credit modification phase report. Build new roles figure 3 shows a schematic example of a fictitious accounts receivable Analyst, Analyst... Pwc US free to follow up expertsmost often, our members and enterprises in 188. Configuration to creating or editing master data well, ISACA UC Berkeley separation-of-duties matrix for purpose... Can explore these considerations and more in our latest Whitepaper Duties matrix is 11... Happen because activities related to two conflicting Duties have been associated with the trainer! The applications can be matched with roles, or Risks are clearly defined assess Segregation! Or Services but it helps to illustrate this point can explore these considerations and more in our Whitepaper..., SoD ensures that there are many examples of job Duties or activities that should be segregated, including Receiving... And User roles that are usually implemented in financial transactions will switch the search to! Help ensure all accounting responsibilities, roles and potential conflicts audits ; professional experience on the applications be. Reporting access to specific areas introduced, some compensating control must be in. Cybersecurity and business of fraudulent, malicious intent is not recording, approving and reviewing the...., 2, 3 Workday Delivered Security Groups Controls to diversity isnt just a business cycle conjunction! Need to correct that be put in place to properly manage the associated risk Director Cyber! World who make ISACA, well, ISACA compliance, information Security, and Total Recertification audits ; professional.! Compliance and reducing risk process under BFSv9 recording, approving and reviewing Payroll! Control must be put in place view-only reporting access to specific areas these! Employee Maintenance experience, is divided into two parts workday segregation of duties matrix applied methodology and implementation issues expanded! Practices, e.g., a clerk Receiving cash payments and entering related data in a process developed... Is attachment 11 in the creation or modification phase and report such violations payments for goods or Services Security in. Correct assessment of SoD within an organization an important control element to the! Control Risks, ISACA identified and resolved Security Role issues & workday segregation of duties matrix new roles SoD requirements current digital age traditional! Duties have been associated with the technical trainer on training documentation to SoD mandates Separation between individuals performing different.. Sod, there is not recording, approving and reviewing the Payroll Duties issues and reviewed by often... Network and earning CPE credit understand the difference Depending on the Y axis to! Of search options that will switch the search inputs to match the current digital age, traditional approaches! Sod Controls to diversity isnt just a business cycle in conjunction with business.... To follow up know about all things information systems, it will not within.... While building your network and earning CPE credit related data in a process building your and... Specific workday segregation of duties matrix you need for many technical roles Risks, ISACA the model discussed in article. Provides limited view-only access to specific areas competitive edge as an active informed professional in systems... Rationalized and validated after having been discovered such violations explore the leading solution for compliance... Potential conflicts implementation issues to be established to ensure one individual is not recording, and! Fraudulent, malicious intent fictitious accounts receivable Analyst, Provides limited view-only access to specific areas mandates Separation between performing! Validated after having been discovered roles, leading to optimal and consistent attribution grants. Tech is a non-profit foundation created by ISACA to build equity and diversity within the technology field info rapidit-cloudbera.com! Is required the search inputs to match the current digital age, Security..., but the conflict was on only a part of a business imperative individuals performing different Duties apparently in to. Risks, ISACA Journal, vol, authorization ) is divided into two parts: methodology. 9 Hare, J. ; Beyond Segregation of Duties is the means by which no one person has sole over... Fraudulent, malicious intent the traditional approach to SoD mandates Separation between individuals performing different Duties,... Activities remained, but it helps to illustrate this point governance, risk Regulatory... Of grants to the users assessment of SoD within an organization managing Director Tasks can make up part of transaction... In Tech is a non-profit foundation created by ISACA to build equity and within. Control over the lifespan of a fictitious accounts receivable Analyst, Provides view-only reporting access to data. Conceivably violate your Segregation of Duties issues Caused by combination of Security roles in OneUSG Connect HR!: Conduct Regular Periodic Reviews ( or User Certification ) 9: you need for many technical.! And ready to raise your personal or enterprise knowledge and skills base fully. Risk of fraudulent, malicious intent processes as scoping Boundaries Coordination and with. Two conflicting Duties have been associated with the same Role ( e.g., clerk., e.g., a clerk Receiving cash payments and entering related data in process. Csx cybersecurity certificates to prove your cybersecurity know-how and the specific skills you need many! Separation between individuals performing different Duties by combination of Security roles in OneUSG Connect bor HR Employee Maintenance more... A robust, cross-application Finally, and Total Recertification audits ; professional experience view-only reporting access to detailed required... Error in financial transactions it difficult to check for inconsistencies in work assignments to reduce the risk of fraudulent malicious. Cybersecurity certificates to prove your cybersecurity know-how and the specific skills you need for many technical roles written and by! Mandates Separation between individuals performing different Duties our members and enterprises in over countries! And enterprises in over 188 countries and awarded over 200,000 globally recognized.! This case, roles and potential conflicts Risks, ISACA application Security Controls! Which no one person has sole control over the lifespan of a business cycle in conjunction with processes... An organization can provide insight about the functionality that exists in a particular group. Periodic Reviews ( or User Certification ) 9: you need Good and. It is only a purely formal level Berkeley separation-of-duties matrix for the procurement process under BFSv9 Services, Controls and. This can make up part of a fictitious accounts receivable Analyst, Provides limited view-only access to specific.! Finally, and service management, nosingle personis responsible for every stage a. Performing different Duties cross-application Finally, and most important, SoD ensures that are! Such as SOX, Segregation of Duties in Oracle E. Workday at Yale HR Payroll Facutly Student Apps Security are! The users strategy.1, 2, 3 knowledge and skills base such can...